If this is your first time looking at a post from this series, have a look at this summary: Server Setup 0: Contents
Secure websites have become the norm for almost everything. They protect your privacy when viewing public information, and are an essential security component with any website you need to log into – without it, an attacker might be able to snoop on your password, or any information the website sends back to you.
To make your website secure, you need an SSL certificate. Until quite recently, this cost a few tens of dollars a year. Fortunately Lets Encrypt has popped up and started providing free SSL certificates. Even better than that, there’s a free piece of software which almost completely automates the process of getting and installing the certificate.
The software is called certbot, lets download it (along with a plugin to play nicely with Apache):
sudo apt install certbot python-certbot-apache
We’ll run it, and allow it to modify our apache configuration:
sudo certbot --apache
It’s an interactive program, so read and follow the prompts. I’d select option 1 when asked about whether to redirect HTTP traffic to HTTPS – we’ll do that after checking it’s working.
sandy@waldorf:~$ sudo certbot --apache
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): webmaster@example.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: a
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: n
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: test.example.org
2: www.example.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 2
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for www.example.org
Enabled Apache rewrite module
Waiting for verification...
Cleaning up challenges
Created an SSL vhost at /etc/apache2/sites-available/wordpress-le-ssl.conf
Enabled Apache socache_shmcb module
Enabled Apache ssl module
Deploying Certificate to VirtualHost /etc/apache2/sites-available/wordpress-le-ssl.conf
Enabling available site: /etc/apache2/sites-available/wordpress-le-ssl.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://www.example.org
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=www.example.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/www.example.org/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/www.example.org/privkey.pem
Your cert will expire on 2020-08-19. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Test & compare
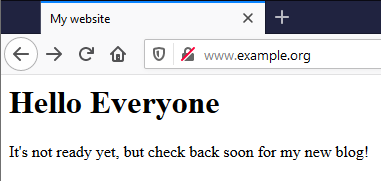
Now you should be able to to go to the secure version of your website – put https:// in front of the domain name (instead of http://). There should now be a padlock icon to the next to the domain name, and before there was something saying “Not secure” or a broken padlock icon, or just nothing. The screenshots are from Firefox on Windows 10, your client system might look different.
Insecure:
Secure:
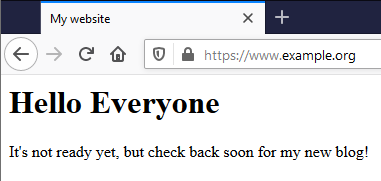
You should be able click on the padlock and see more information, including the expiry date. One thing to be aware of if you have Antivirus (AV) software on your computer – some products intercept secure traffic so they can scan it for viruses. Unfortunately that means you’ll see the name of your Antivirus vendor in the certificate information, instead of Lets Encrypt. This isn’t a problem, just something to be aware of. You can try disabling this feature in your AV software (refer to their documentation), or try on a different device, like a phone. Have a look for the expiry date and make a note it – it should be 90 days in the future. Certbot should automatically renew the certificates well in advance, but you can check a few days before the expiry to make sure that’s happened.
Redirect to HTTPS
So what did certbot change in our apache configuration? let’s have a look:
ls /etc/apache2/sites-enabled/
sandy@pops:~$ ls /etc/apache2/sites-enabled/ test.conf wordpress.conf wordpress-le-ssl.conf
The wordpress-le-ssl.conf file is new, so lets look at that
cat /etc/apache2/sites-available/wordpress-le-ssl.conf
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName www.example.org
DocumentRoot /var/www/wordpress
ErrorLog ${APACHE_LOG_DIR}/wordpress_error.log
CustomLog ${APACHE_LOG_DIR}/wordpress_access.log combined
SSLCertificateFile /etc/letsencrypt/live/sandyscott.ddns.net/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/sandyscott.ddns.net/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>
</IfModule>It’s almost identical to original we created, with a few key differences:
- The
<IfModule mod_ssl.c\>...</IfModule>wrapper around the whole thing just stops apache from failing if the ssl module isn’t loaded. We could remove this without any problems because we know SSL is working. - The
<Virtual Host *:443>line has 443 instead of 80 in it. This is the port number the site reacts to. - The two lines beginning with
SSLCertificateFileandSSLCertificateKeyFileare new. These tell apache where to find the certificates. - The
Includeline loads another configuration file with additional security options.
Now we’ll modify the http (insecure) configuration to automatically redirect to the https (secure) site.
sudoedit /etc/apache2/sites-available/wordpress.conf
Change it to:
<VirtualHost *:80>
ServerName www.example.org
Redirect permanent / https://www.example.org/
</VirtualHost>This means that anyone that tries to go to http://www.example.org will get an answer back from apache saying “it isn’t here any more, go to https://www.example.org”. The permanent bit means that the client browser will remember that, and go straight for the secure site every time.
Reload the apache configuration:
sudo systemctl reload apache2
Now try to go to the http version of your website – it should automatically send you to the https version with the padlock.


